Our Software Solutions
Paradigm exclusively serves the building industry, so we’ve developed our solutions with your unique challenges in mind.
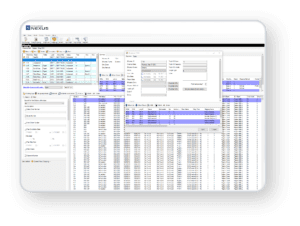
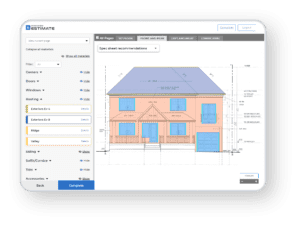
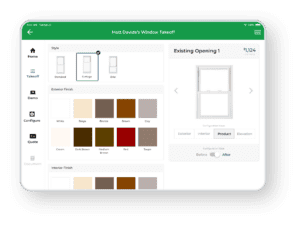
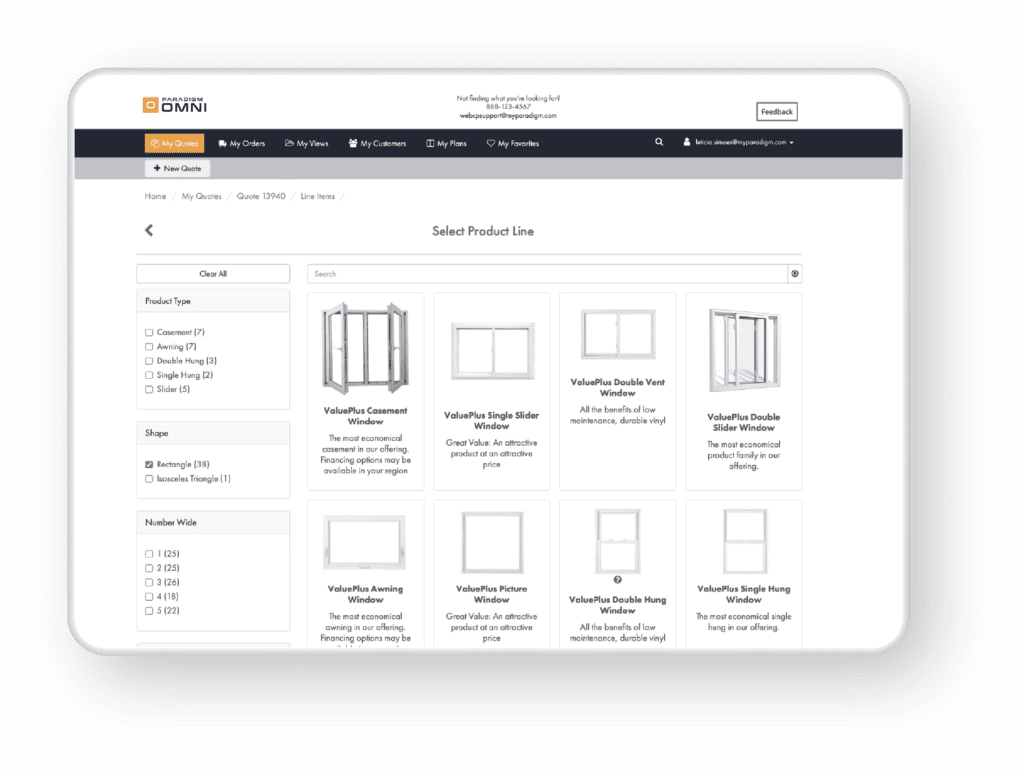
The building industry’s leading CPQ solution for quoting complex products. This omni-channel selling solution offers online, in-home, in-store, and dealer functionality to help you maximize your sales and reduce your tech stack.
Solutions for Every Business
Paradigm’s software solutions help organizations throughout the supply chain to boost sales, reduce costs, and become more competitive.
A word from Paradigm’s President on Our Commitment to the Industry.
Watch Video
Your Success is Our Success
With a technology platform that sets the bar for the building industry around the world, Paradigm is committed to driving innovation and helping renovation contractors, dealers, lumberyards, distributors and retailers achieve their goals.
0+
Paradigm Employees
0+
Customers
0+
End Users
0%
Customer Satisfaction
Our Trusted Window & Door Manufacturer Brands














Trusted by Manufacturers









Trusted by Distributors, Retailers & Dealers








Trusted by Homebuilders






Our Industry Partners






Paradigm – In Our Customers’ Word
Watch Video
News and Insights
Read the latest on Paradigm’s events, technology, and culture.
Navigating Technology Upgrades
In the realm of window and door manufacturing, staying ahead often involves significant technology shifts.
Paradigm Announces Threekit Partnership
Paradigm’s partnership with Threekit adds a 3D configuration for customers to create and view personalized window and door configurations in real time.